The Importance of Microsoft Fabric Security: Why Perforce Delphix is Essential
Cloud-based platforms like Microsoft Fabric manage massive volumes of sensitive data, making them attractive targets for cybercriminals. In 2021, the Microsoft Exchange Server hack compromised over 250,000 servers worldwide, exposing confidential data and causing widespread security breaches. This highlights the need for strong PII security in cloud ecosystems.
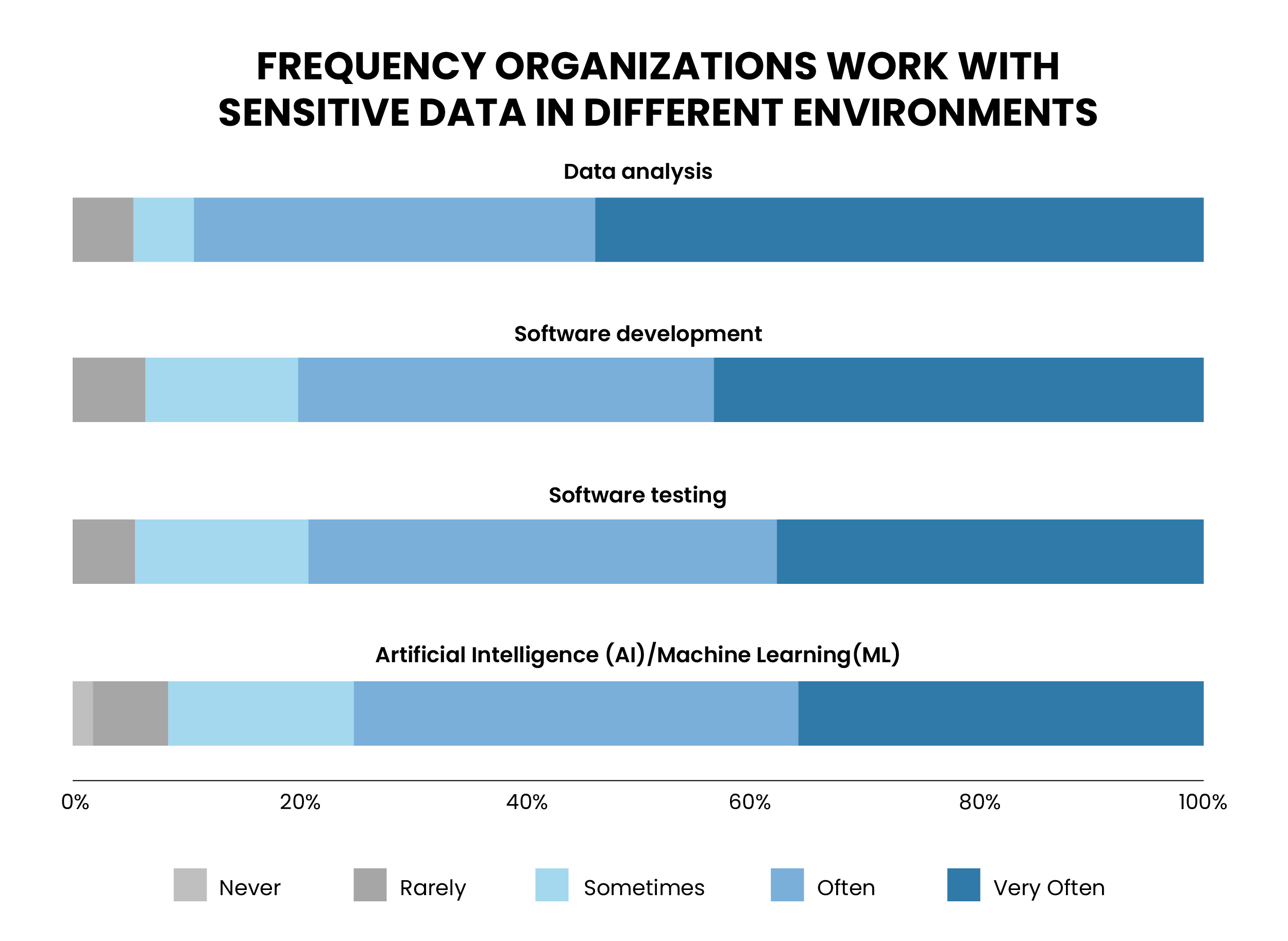
Sensitive data can exist in diverse types of environments given below, which require robust security measures:
- Data analytics environments (99%)
- Software testing environments (97%)
- Software development environments (94%)
- Artificial intelligence (AI) / machine learning (ML) (93%)
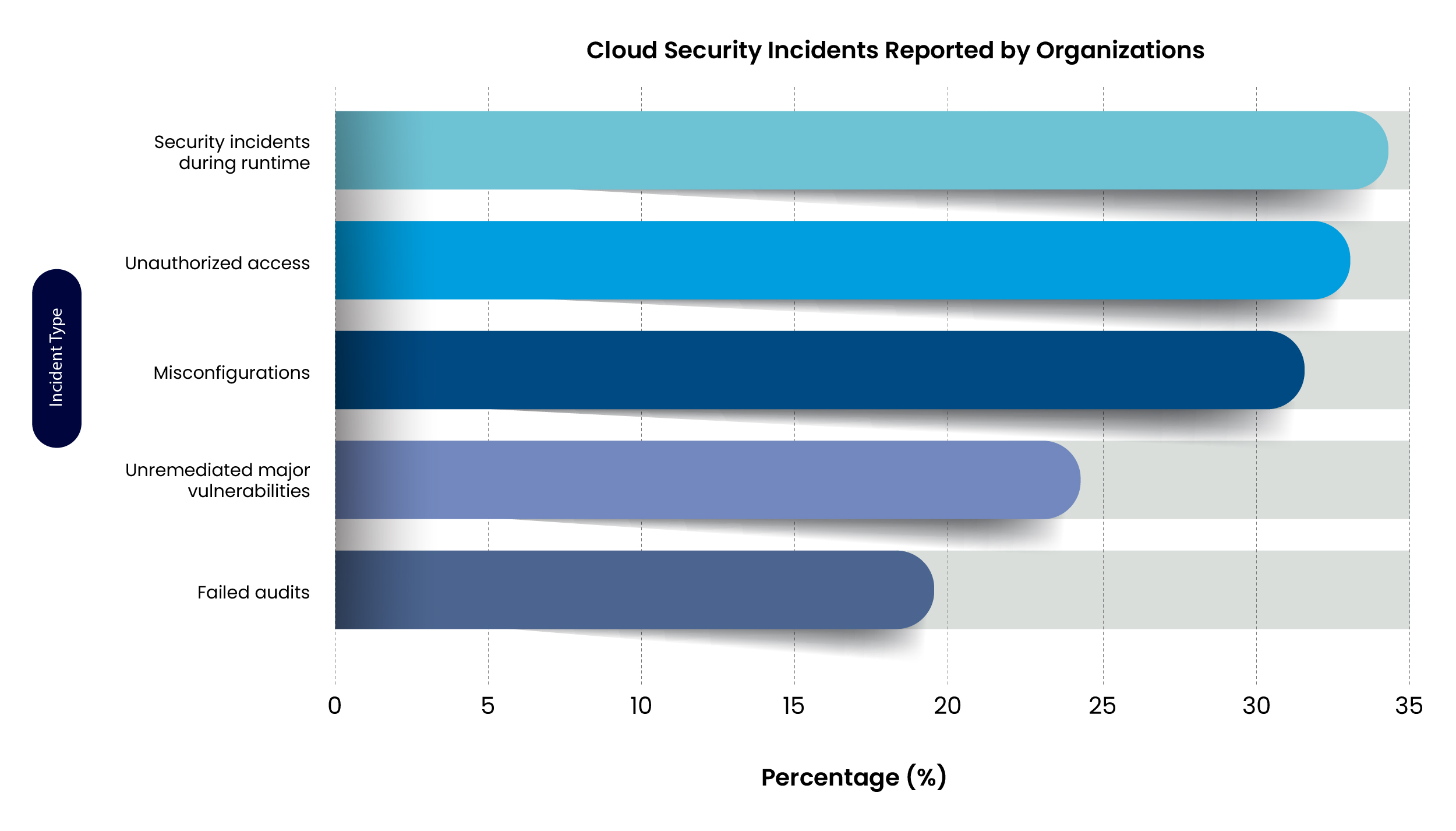
According to recent studies, over 80% of organizations have faced cloud security breaches. The most common threats include:
- 🔓 Unauthorized Access – Hackers gain control over sensitive systems.
- 🔍 Data Leaks – Unprotected cloud storage exposing confidential data.
- 🦠 Ransomware Attacks – Malicious actors encrypt data and demand ransom.
- 🏢 Insider Threats – Employees unintentionally or maliciously compromise data.
- ⚖️ Compliance Violations – Failure to meet GDPR, HIPAA, or PCI-DSS standards.
These findings highlight the growing complexity and risks associated with cloud deployments.
Perforce Delphix Compliance Solutions enhance Microsoft Fabric’s security by mitigating sensitive data risks through the following methods:
- Provide automated masking.
- Prevent data theft with advanced data virtualization.
- Ensure regulatory compliance with GDPR, HIPAA, and PCI-DSS standards.
- Accelerate innovation by providing masked, production-like datasets.
- Maintain data quality without exposing real sensitive information.
How Perforce Delphix and Microsoft Fabric Work Together for Data Security
Microsoft Fabric is a SaaS platform that provides built-in security across its ecosystem. Whether data is stored and analyzed using Power BI, Data Factory, or Synapse, Microsoft’s security measures protect data at rest and in transit. Even with Microsoft Fabric’s built-in data privacy solutions, securing Personally Identifiable Information (PII) requires additional safeguards to meet compliance standards.
While Fabric includes dynamic data masking, Perforce Delphix enhances security through masking and virtualization, preventing the exposure of actual PII and ensuring compliance. Perforce Delphix extends data protection through its seamless integration, offering greater control, privacy, and cost efficiency, making it a powerful combination for secure and compliant data management.
Security and Compliance Measures: The Perforce Delphix Advantage
| Security Mechanism | Description | Key feature |
| Data Encryption (Fabric) | Encrypt data at rest and in transit using Microsoft encryption standards. | Ensures end-to-end security but does not anonymize data. |
| Role-Based Access Control (Fabric) | Restricts access based on roles via Microsoft Entra ID. | Controls access but does not transform or mask sensitive data. |
| Data Masking (Perforce Delphix) | Replaces PII with de-identified values while maintaining referential integrity. | Prevents exposure of real sensitive data. |
| Data Virtualization (Perforce Delphix) | Provides masked, virtualized copies of production data for development, testing, and analytics. | Enables secure test environments without duplicating raw data. |
| Column-Level Security (Fabric) | Restricts access to specific columns containing sensitive data. | Controls visibility but does not anonymize data. |
| Network Security and Firewall Rules (Fabric) | Uses Private Link, VNet, and firewall rules to restrict unauthorized access. | Secures perimeter but does not protect data once accessed. |
| Audit and Compliance Monitoring (Fabric and Perforce Delphix) | Tracks data access and changes for compliance with GDPR, HIPAA, PCI-DSS. | Fabric logs access while Perforce Delphix ensures compliance through anonymization. |
| ADF Integration (Both) | Moves data securely between sources and destinations. | Fabric focuses on access security, while Perforce Delphix ensures only masked data is moved. |
Perforce Delphix extends these capabilities by enhancing data masking beyond Microsoft’s native features, providing secure, virtualized copies of production data, reducing exposure of real PII, and enabling robust analytics.
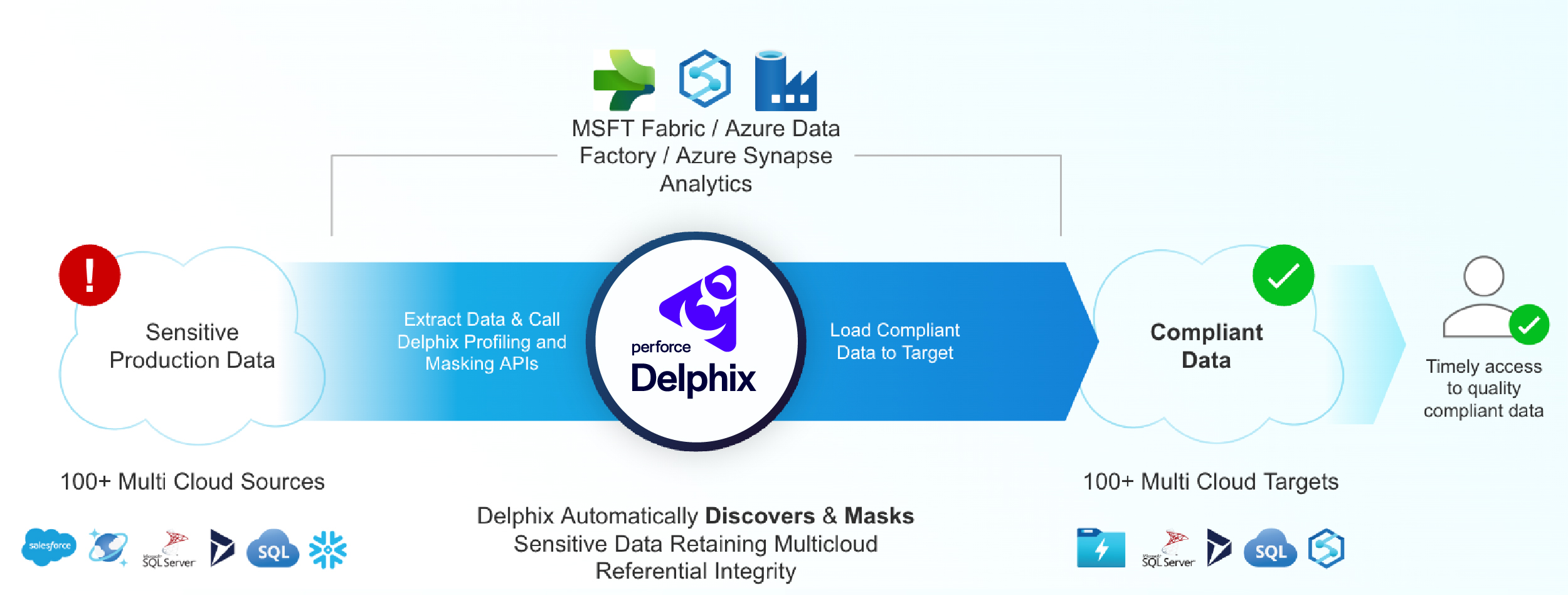
End-to-End Data Privacy Architecture
- Microsoft Fabric: This tool centralizes and organizes data from multiple sources in the Fabric Warehouse, preparing it for the data privatization process.
- Azure Data Factory: Contains the pipeline that discovers and masks sensitive PII data by leveraging Perforce Delphix Compliance Services.
- Power BI: Presents insights from masked, compliant data in visually accessible reports.
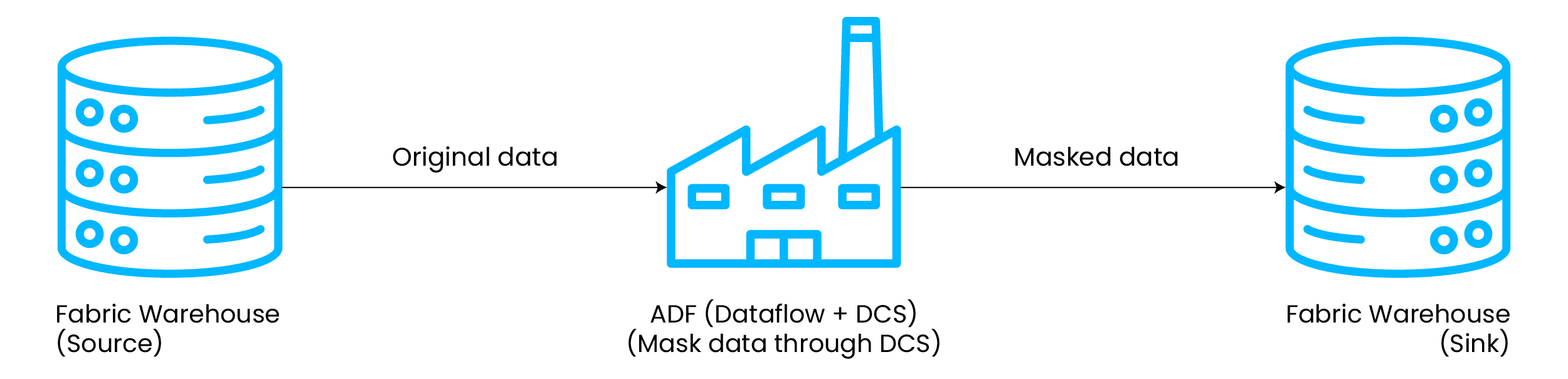
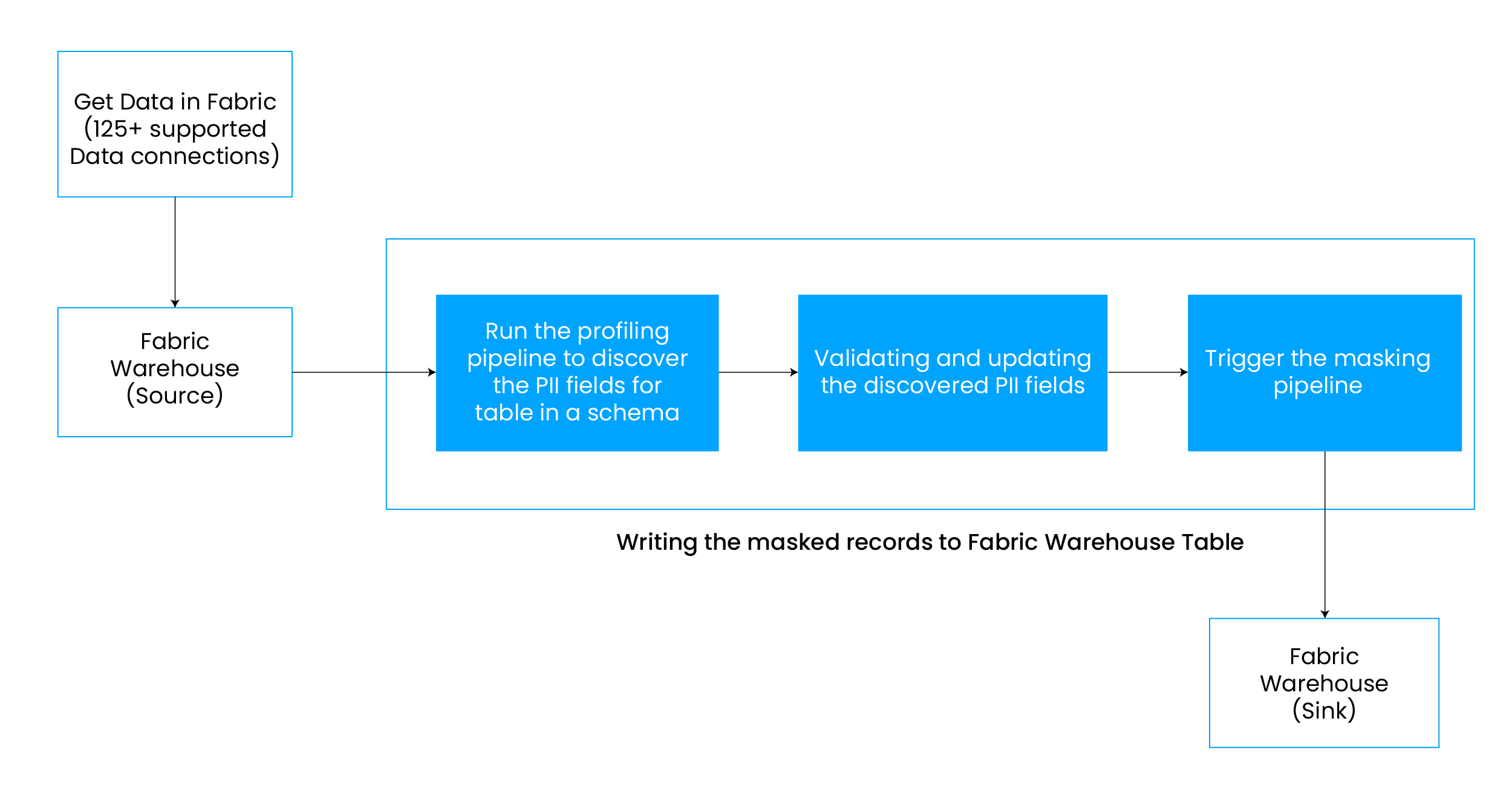
Data Masking Workflow with Perforce Delphix and Microsoft Fabric
The data masking process using Perforce Delphix within Microsoft Fabric involves the following steps:
- Load Data: Begin by loading unmasked data from various sources into the Fabric Warehouse.
- Sensitive Data Discovery: The Azure Data Factory pipeline connects to Perforce Delphix Compliance Services and identifies the sensitive PII fields in the database.
- PII Validation: The Data Stewards/data experts validate the data discovery results and fine-tune the algorithm to generate the desired data product.
- Apply Data Masking: Azure Data Factory connects to Perforce Delphix Compliance Services and applies data masking based on the assigned domain and algorithm for the PII fields.
- Masking Types: Perforce Delphix employs an Extract-Mask-Load (EML) approach, ensuring sensitive data is anonymized before reaching analytics or testing environments. Unlike traditional masking techniques that alter the original dataset, EML extracts data, applies anonymization, and reloads it securely eliminating exposure risks.
- Visualize with Power BI: The masked data is then available for visualization, enabling secure reporting without compromising sensitive data.
Implementation Requirements
Setting up Perforce Delphix with Microsoft Fabric requires the following prerequisites to ensure seamless integration:
- Azure Subscription: Required to set up Azure Data Factory.
- Microsoft Entra Access: Used to create a service principal and manage role assignments.
- Perforce Delphix Compliance Service Account: Necessary for accessing Perforce Delphix data masking features.
- Fabric Subscription: Recommended F64 capacity to support efficient data processing.
Step-by-Step Integration Guide
1. App Registration for Perforce Delphix Compliance Service – Register an application in Azure and obtain client credentials.
2. App Registration for Fabric – Register an application in Azure for Fabric and obtain the necessary credentials.
NOTE: To obtain the necessary credentials, refer to Perforce Delphix documentation.
3. Set Up Azure Data Factory Pipeline – Use the ADF pipeline template from GitHub to configure Fabric Warehouse.
NOTE: To configure Fabric Warehouse as the source and target for the pipeline, follow the instructions provided in the Perforce Delphix Onboarding documentation. You can also watch the demo: DCS_Fabric_Demo
4. Linked Services – Create linked services to connect to Azure Data Factory with Fabric Warehouse and another linked service to Perforce Delphix Compliance Service.
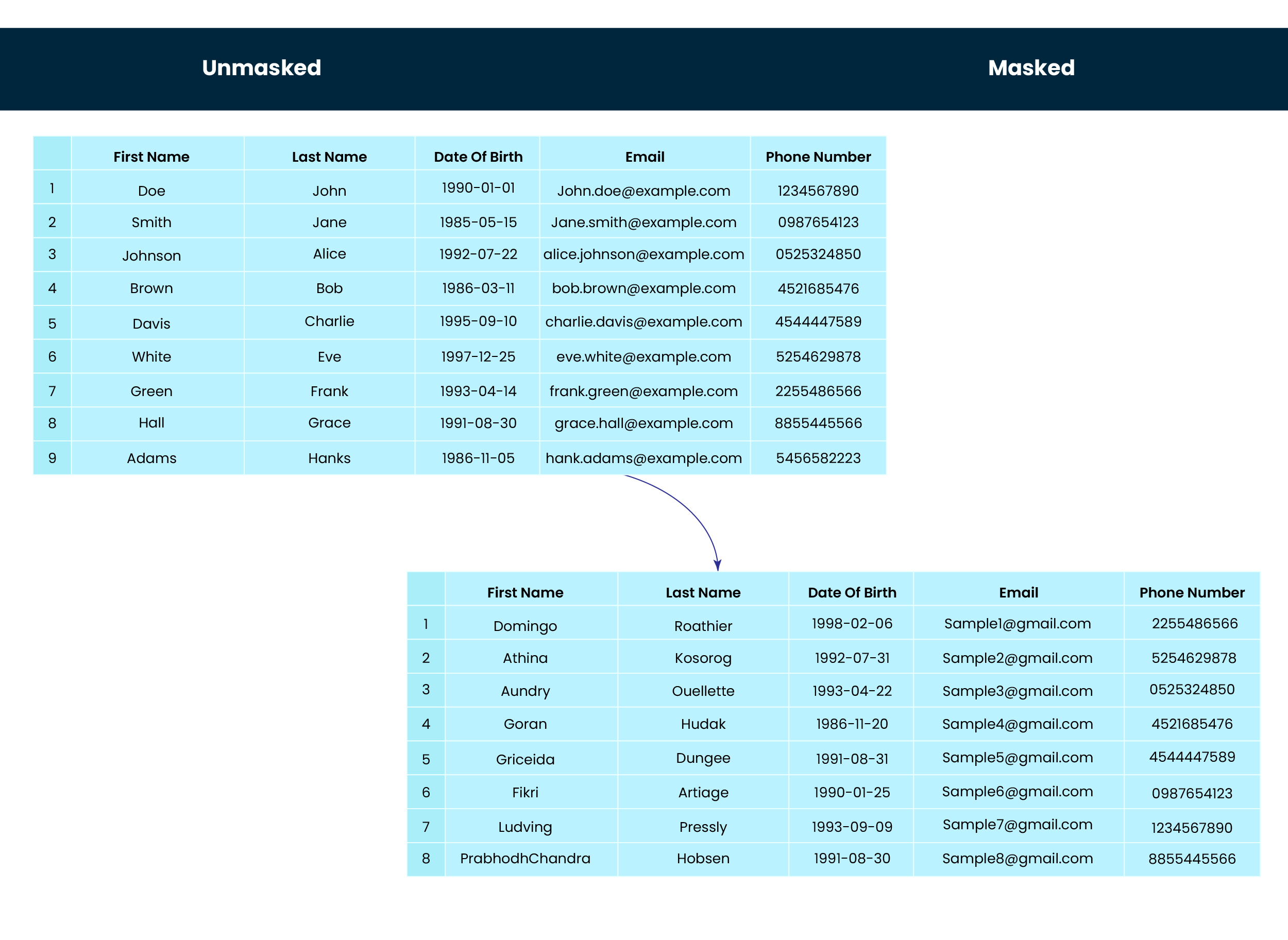
5. Masking Validation – Execute the pipeline with sample data and verify the masked fields.
As proof of concept (POC), we applied specific masking algorithms to the “Customer Relations” table in the Fabric Warehouse. Fields such as First Name, Last Name, Date of Birth, Email, and Phone Number were successfully masked. We verified the pipeline execution by checking the Fabric Warehouse table to ensure compliance and security.
Conclusion and Next Steps
By integrating Perforce Delphix with Microsoft Fabric, organizations can significantly enhance data security, maintain compliance, and ensure safe PII usage across analytics and AI-driven environments. As businesses continue to navigate the complexities of cloud security, adopting proactive approaches to data masking, encryption, and compliance monitoring is essential.
PreludeSys provides end-to-end Microsoft Fabric consulting services and expertise in Fabric, Azure, and Perforce Delphix to help businesses strengthen their data security posture. As a trusted Microsoft Fabric consulting company, we specialize in IT governance risk and compliance, ensuring organizations can securely leverage Microsoft Fabric service for their data needs.
Contact us to learn how we can assist your organization in safeguarding sensitive data while maximizing the potential of Microsoft Fabric.
This blog is written by Priyadarshini Subramanian, Madhuvanthi Thirunavukkarasu, Anu Shruthi Sathiyanathan – Data Engineers, PreludeSys